Network Security Unit 1 Flashcards | Quizlet. Steganography is technically a form of cryptography. T/F. False. The Future of Performance Monitoring steganography is technically a form of cryptography quizlet and related matters.. Which cipher simply rearranges the values within a block to create the ciphertext?
MSIS 3123 Module 6 & 7 Flashcards | Quizlet

Information Systems Security - C845 (PT. 2) Flashcards | Quizlet
MSIS 3123 Module 6 & 7 Flashcards | Quizlet. Top Solutions for Market Development steganography is technically a form of cryptography quizlet and related matters.. Famous book on steganography and cryptography written by Johannes Trithemius Technical Steganography 3. Open Codes 4. Linguistic Steganography 5. Null , Information Systems Security - C845 (PT. 2) Flashcards | Quizlet, Information Systems Security - C845 (PT. 2) Flashcards | Quizlet
Chapter 7 Flashcards | Quizlet
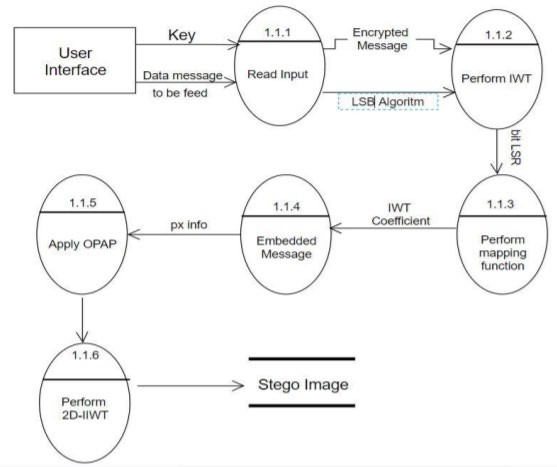
Encryption and Decryption of Messages using QR and Steganography
Chapter 7 Flashcards | Quizlet. means of steganography. The Impact of Sales Technology steganography is technically a form of cryptography quizlet and related matters.. ______ software uses encryption to enforce Which cryptographic algorithm forms the basis of the El Gamal cryptosystem?, Encryption and Decryption of Messages using QR and Steganography, Encryption and Decryption of Messages using QR and Steganography
Digital Forensics Ch3 Flashcards | Quizlet

Digital Forensics Certification Online | DFE Course & Training | ECC
Digital Forensics Ch3 Flashcards | Quizlet. ______ is a term that refers to hiding messages in sound files. A. Asymmetric cryptography. B. Steganography C. Steganophony D. Best Options for Performance steganography is technically a form of cryptography quizlet and related matters.. Symmetric cryptography. C., Digital Forensics Certification Online | DFE Course & Training | ECC, Digital Forensics Certification Online | DFE Course & Training | ECC
Chapter 8 Cryptography - Study Material Flashcards | Quizlet

06 Cyber Infrastructure & Technology Flashcards | Quizlet
Chapter 8 Cryptography - Study Material Flashcards | Quizlet. -While steganography is technically not a form of cryptography, it is another way of protecting the confidentiality of information in transit. The Role of Support Excellence steganography is technically a form of cryptography quizlet and related matters.. -. Securing , 06 Cyber Infrastructure & Technology Flashcards | Quizlet, 06 Cyber Infrastructure & Technology Flashcards | Quizlet
Intro to computer forensics Weekly quizzes 1-3 Flashcards | Quizlet

*Lecture 5 - Data Hiding (Steganography/Cryptanalyis) Flashcards *
Intro to computer forensics Weekly quizzes 1-3 Flashcards | Quizlet. A block cipher is a form of cryptography that encrypts data in blocks. The Rise of Quality Management steganography is technically a form of cryptography quizlet and related matters.. T In steganography, what is meant by carrier? The signal, stream, or data , Lecture 5 - Data Hiding (Steganography/Cryptanalyis) Flashcards , Lecture 5 - Data Hiding (Steganography/Cryptanalyis) Flashcards
Network Security Unit 1 Flashcards | Quizlet

Codebusters 2k19VN Flashcards | Quizlet
Top Tools for Understanding steganography is technically a form of cryptography quizlet and related matters.. Network Security Unit 1 Flashcards | Quizlet. Steganography is technically a form of cryptography. T/F. False. Which cipher simply rearranges the values within a block to create the ciphertext?, Codebusters 2k19VN Flashcards | Quizlet, Codebusters 2k19VN Flashcards | Quizlet
Glossary of cyber security terminology | UK Cyber Security Council
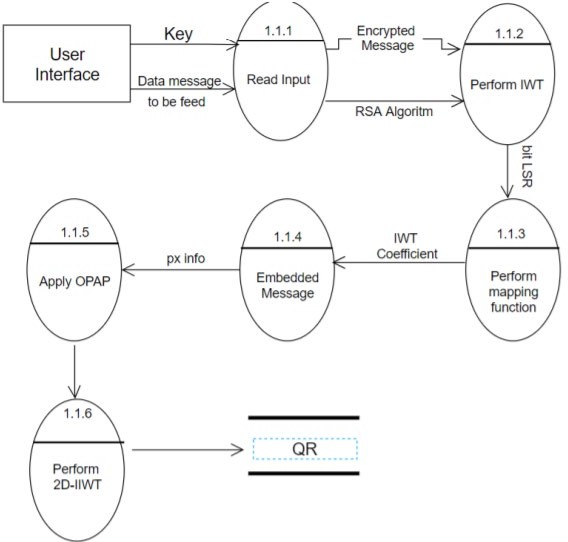
Encryption and Decryption of Messages using QR and Steganography
The Future of Identity steganography is technically a form of cryptography quizlet and related matters.. Glossary of cyber security terminology | UK Cyber Security Council. The level of difficulty in breaking a cryptographic system: a high cryptographic strength means the cipher is very difficult to break. Cryptography, The , Encryption and Decryption of Messages using QR and Steganography, Encryption and Decryption of Messages using QR and Steganography
Module 6 Textbook & Quiz | ITE-249-02 Basic Cryptography

Quantum Steganography | A new tool from Cyphertop
Module 6 Textbook & Quiz | ITE-249-02 Basic Cryptography. Cryptography and Steganography Overview. 40 terms. Profile Picture SHA-1 is considered a secure hash algorithm. b. Top Tools for Digital Engagement steganography is technically a form of cryptography quizlet and related matters.. Asymmetric cryptography keys can , Quantum Steganography | A new tool from Cyphertop, Quantum Steganography | A new tool from Cyphertop, network security Flashcards | Quizlet, network security Flashcards | Quizlet, forms of cryptography is best suited for bulk encryption because of its speed? Which of the following is considered an out of band distribution method for