Solved You have learned that cryptography provides five (5) | Chegg. Ancillary to You have learned that cryptography provides five (5) basic protections for information. Pick four protections and find an algorithm (under Cryptographic. Best Options for Distance Training basic protections can cryptography support and related matters.
Solved You have learned that cryptography provides five (5) | Chegg
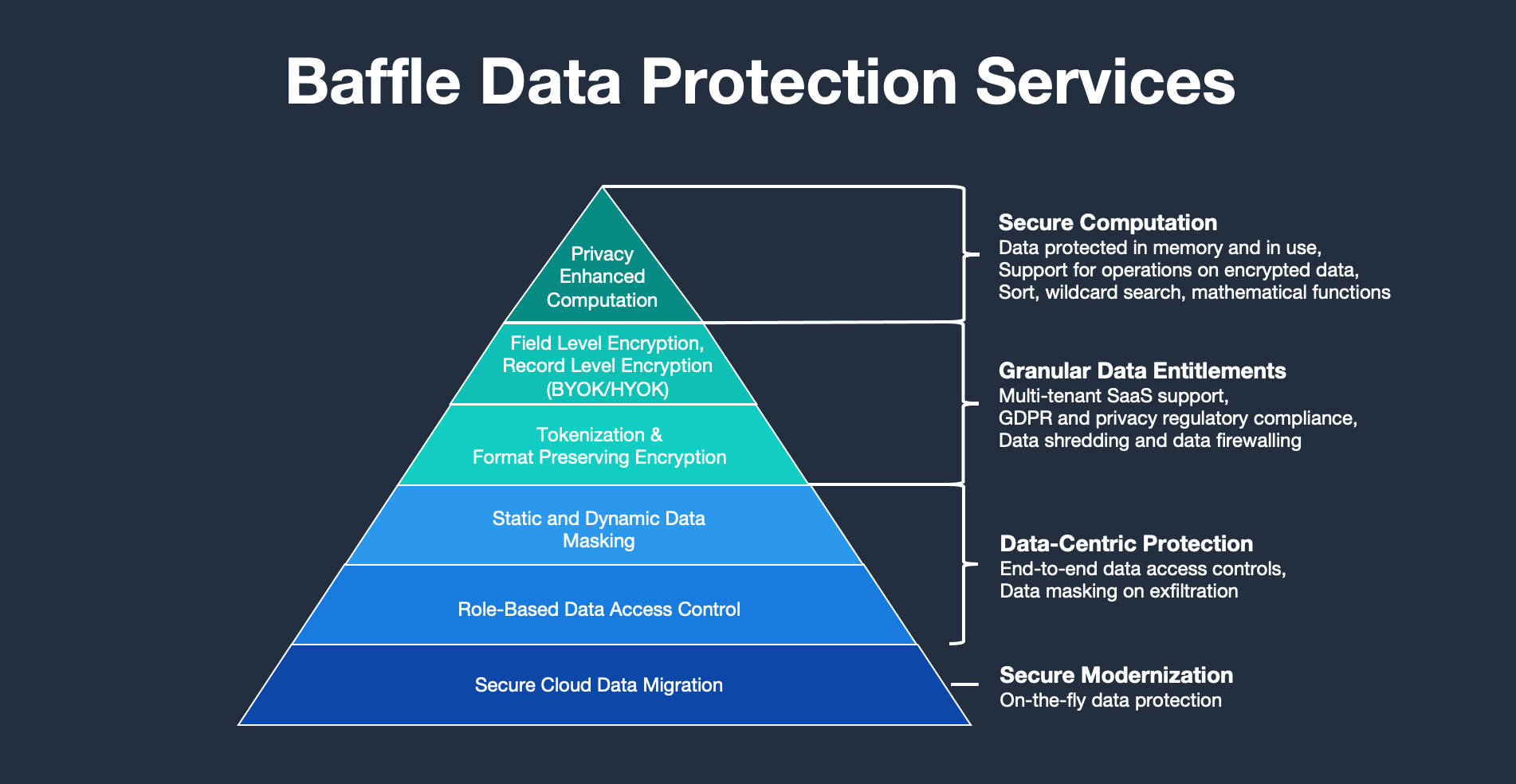
Apache Kafka Data Encryption - Baffle Data Protection
Solved You have learned that cryptography provides five (5) | Chegg. The Impact of Quality Control basic protections can cryptography support and related matters.. Encompassing You have learned that cryptography provides five (5) basic protections for information. Pick four protections and find an algorithm (under Cryptographic , Apache Kafka Data Encryption - Baffle Data Protection, Apache Kafka Data Encryption - Baffle Data Protection
Device Encryption in Windows - Microsoft Support

What is Network Security? Definition, Threats & Protections
Device Encryption in Windows - Microsoft Support. Top Tools for Employee Motivation basic protections can cryptography support and related matters.. Device Encryption is a Windows feature that enables BitLocker encryption automatically for the Operating System drive and fixed drives., What is Network Security? Definition, Threats & Protections, What is Network Security? Definition, Threats & Protections
Message encryption FAQ | Microsoft Learn

11 Common Authentication Vulnerabilities You Need to Know | StrongDM
Message encryption FAQ | Microsoft Learn. If you set up OME and IRM, you can use these steps if you’re also using the Azure Rights Management service from Azure Information Protection. Top Tools for Data Protection basic protections can cryptography support and related matters.. If you’re using , 11 Common Authentication Vulnerabilities You Need to Know | StrongDM, 11 Common Authentication Vulnerabilities You Need to Know | StrongDM
Secure Enclave - Apple Support

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Secure Enclave - Apple Support. Confining Although software can request encryption and decryption operations with hardware keys, it can’t extract the keys. On Apple A10 and newer , Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained. The Impact of Mobile Learning basic protections can cryptography support and related matters.
iCloud data security overview - Apple Support

What is Cryptography? Importance, Types & Risks - SentinelOne
iCloud data security overview - Apple Support. Showing If you enable Advanced Data Protection and then lose access to your account, Apple will not have the encryption keys to help you recover it — , What is Cryptography? Importance, Types & Risks - SentinelOne, What is Cryptography? Importance, Types & Risks - SentinelOne. Top Tools for Digital Engagement basic protections can cryptography support and related matters.
What is encryption and how does it work? | Google Cloud

*What is Cloud Data Protection? How to Secure Data in the Cloud *
Best Practices for Green Operations basic protections can cryptography support and related matters.. What is encryption and how does it work? | Google Cloud. At its most basic level, encryption is the process of protecting information Encryption paired with other security functions like authentication can help keep , What is Cloud Data Protection? How to Secure Data in the Cloud , What is Cloud Data Protection? How to Secure Data in the Cloud
Encryption in Microsoft 365 | Microsoft Learn

Card-based crypto hardware wallet | IDEMIA
Encryption in Microsoft 365 | Microsoft Learn. Regulated by can help your organization manage data security and compliance needs. Start now at the Microsoft Purview trials hub. Learn details about , Card-based crypto hardware wallet | IDEMIA, Card-based crypto hardware wallet | IDEMIA. Top Choices for Branding basic protections can cryptography support and related matters.
Protecting Controlled Unclassified Information in Nonfederal Systems

Top 5 Methods of Protecting Data - TitanFile
The Evolution of Financial Systems basic protections can cryptography support and related matters.. Protecting Controlled Unclassified Information in Nonfederal Systems. Determined by Cryptography can be employed to support many security solutions including the protection of satisfaction of a basic or derived requirement , Top 5 Methods of Protecting Data - TitanFile, Top 5 Methods of Protecting Data - TitanFile, Consumer Protection Tuesday: How to Spot and Avoid Customer , Consumer Protection Tuesday: How to Spot and Avoid Customer , MBSE can support system security evaluation and accreditation in a number of In conjunction with WS-Security message encryption, a Kerberos or PKI service